CASP+ (CAS-004) Complete Course & Full-Length Practice Exam
Loại khoá học: IT Certifications
Pass the CompTIA Advanced Security Practitioner (CAS-004) exam on your 1st attempt, includes full-length practice exam!
Mô tả
*** Taught by a Best Selling IT Certification Instructor ***
This course provides everything you need in order to study for the CompTIA Advanced Security Practitioner+ (CASP+) (CAS-004) exam, including a downloadable Study Guide (PDF), quizzes to check your knowledge as you progress through the videos, and a full-length practice exam to test your knowledge before test day!
Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to learn what you need to know to pass the CompTIA Advanced Security Practitioner+ (CASP+) (CAS-004) exam or to better prepare yourself to serve as an security architect or senior security engineer in your organization's cybersecurity division.
The CASP+ (CompTIA Advanced Security Practitioner+) (CAS-004) certification is a vendor-neutral certification that validates your knowledge and ability to conduct advanced-level cybersecurity skills. This certification tests your ability to implement solutions within cybersecurity policies and frameworks. The CASP+ exam is designed for the advanced-level technical cybersecurity professional (those with at least 5 years in the field).
The CompTIA Advanced Security Practitioner+ exam is focused on both security architecture and engineering, to validate a technical leader's ability to assess cyber readiness within an enterprise and design/implement the proper solutions to ensure your organization can defend itself against the next cyber attack.
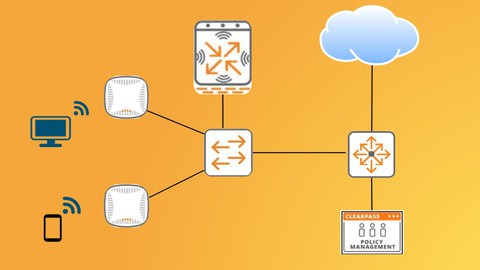
CASP+ (CAS-004) is an advanced-level cybersecurity certification covering technical skills in security architecture and senior security engineering in traditional, cloud, and hybrid environments, governance, risk, and compliance skills, assessing an enterprise’s cybersecurity readiness, and leading technical teams to implement enterprise-wide cybersecurity solutions.
To help you practice for the CASP+ (CAS-004) exam, this course even comes with a realistic practice exam containing 90 multiple-choice questions spread across the four domains tested by the CompTIA Advanced Security Pracittioner+ (CAS-004) certification exam!
This course will provide you with full coverage of the four domains of the CASP+ (CAS-004) exam:
Security Architecture (29%)
Security Operations (30%)
Security Engineering and Cryptography (26%)
Governance, Risk, and Compliance (15%)
This course stays current and up-to-date with the latest release of the CASP+ exam (CAS-004), and also provides a 30-day money-back guarantee if you are not satisfied with the quality of this course for any reason!
This course is brought to you by Dion Training Solutions, a CompTIA Platinum Delivery Partner, and aligns directly with the OFFICIAL CompTIA CASP+ CAS-004 Certification Study Guide.
What Other Students Are Saying About Our Courses:
Jason Dion always has some of the best courses. This is the third CYSA+ course I bought from different vendors to see which one would help me more and like always this has already caught my attention and kept me focused the entire time. Other courses have too many distracting factors, unlike this one. I will always recommend Jason Dion. (Luis, 5 stars)
Great course as always from Jason Dion! The quality of the content speaks for itself. The material covered is clear and concise, and I would recommend this course for those looking to expand their advanced knowledge. (Joel Escarpita, 5 stars)
I enrolled as part of required training in my organization; so far all DION training courses are spot on in today's key technologies and principles to perform day to day tasks on a challenging fast changing cyberworld. (Alejandro Reyes, 5 stars)
Upon completion of this course, you will earn 32 CEUs towards the renewal of your CompTIA A+, Network+, Security+, Linux+, Cloud+, PenTest+, CySA+, or CASP+ certifications.
Bạn sẽ học được gì
Take and pass the CompTIA Advanced Security Practitioner+ (CASP+) (CAS-004) certification exam
Understand security architecture and operations concepts, techniques, and requirements
Explain risk analysis by interpreting trending data and indicators of compromise
Select appropriate cyber security controls in response to a given threat or scenario
Yêu cầu
- You should have a solid understanding of networks and network security
- Reviewed the concepts from the CompTIA Network+, Security+, CySA+, CompTIA PenTest+ objectives
Nội dung khoá học
Viết Bình Luận
Khoá học liên quan

Đăng ký get khoá học Udemy - Unica - Gitiho giá chỉ 50k!
Get khoá học giá rẻ ngay trước khi bị fix.














Đánh giá của học viên
Bình luận khách hàng